Splunk's Boss of the SOC is essentially a blue-team oriented capture-the-flag. The yearly competition challenges teams to race through incident response questions for multiple scenarios while leveraging Splunk's dashboard. Knowledge of SPL (Splunk Search Processing Language) and usage of their dashboard is obviously useful. The incidents also necessitate know-how in networking, Windows (specifically Windows Events and Sysmon), Linux, and an understanding of how and when to use the multitude of log data that includes multiple sources.
Splunk publishes these challenges online for anyone to try, outside of the competitions. Here you can find Version 1 in an interactive format, it includes two scenarios with a 4 hour time limit. At the end of those 4 hours, you receive a score based on how many questions you answered, how quickly, and how many times you gave a wrong answer.
This post is specifically about Scenario 2: Ransomware. Here's the background information for the scenario:
"After the excitement of yesterday, Alice has started to settle into her new job. Sadly, she realizes her new colleagues may not be the crack cybersecurity team that she was led to believe before she joined. Looking through her incident ticketing queue she notices a “critical” ticket that was never addressed. Shaking her head, she begins to investigate. Apparently on August 24th Bob Smith (using a Windows 10 workstation named we8105desk) came back to his desk after working-out and found his speakers blaring (click below to listen), his desktop image changed (see below) and his files inaccessible.
Alice has seen this before... ransomware. After a quick conversation with Bob, Alice determines that Bob found a USB drive in the parking lot earlier in the day, plugged it into his desktop, and opened up a word document on the USB drive called "Miranda_Tate_unveiled.dotm". With a resigned sigh she begins to dig into the problem..."
Along with a Splunk server to log into, you are given several resources to aid you in answering the questions. The resources include a screenshot of the ransomware, a summary of the source types available, a reference guide, and more. There are 12 questions for Scenario 2. Some of the screenshots are a bit blurry so I made sure to clearly specify the correct answers.
Below are two examples of the resources provided:
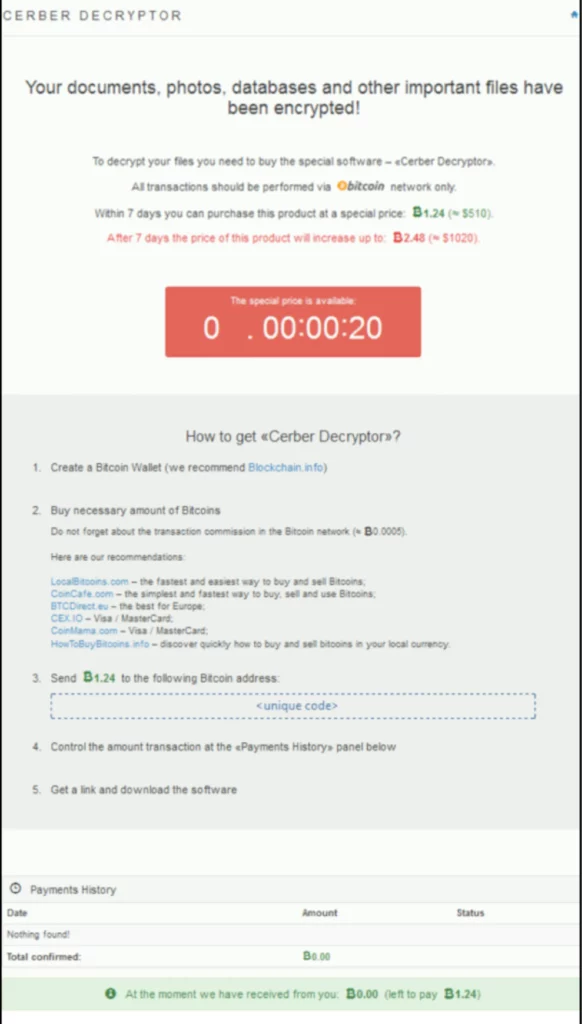
Question 1: What was the most likely IPv4 address of we8105desk on 24AUG2016?
We begin by trying to find out information about we8105desk, Bob's machine with the Date time range set to events occurring on Aug 24 2016. The Date time range will stay consistent throughout our search as the attack occurred on that day.
index="botsv1" source="WinEventLog:System" host="we8105desk"We find that his machines name on the network is we8105desk.waynecorpinc.local. We can search for that hostname as the destination, in any WinEventLog source, where the field "dest_ip" has a value.
index="botsv1" dest="we8105desk.waynecorpinc.local" source="WinEventLog:*" dest_ip="*"This returns 122 events and at the top, we find a Sysmon event from Aug 24th, with Bobs IP.
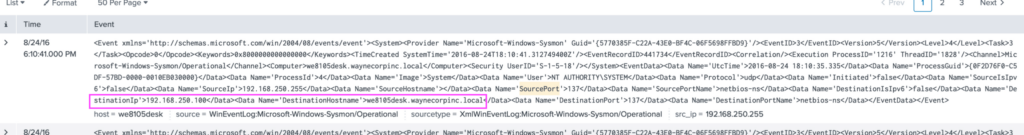
Answer: The likely IP of we8105desk at the time of the attack was 192.168.250.100.
Question 2: Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times? Submit ONLY the signature ID value as the answer.
We can take a quick look over the Suricata logs to identify which fields will be useful to us to optimize our query. You can also use the fieldsummary command to a get table of the available fields.
index="botsv1" source="/var/log/suricata/eve.json"index="botsv1" source="/var/log/suricata/eve.json" | fieldsummary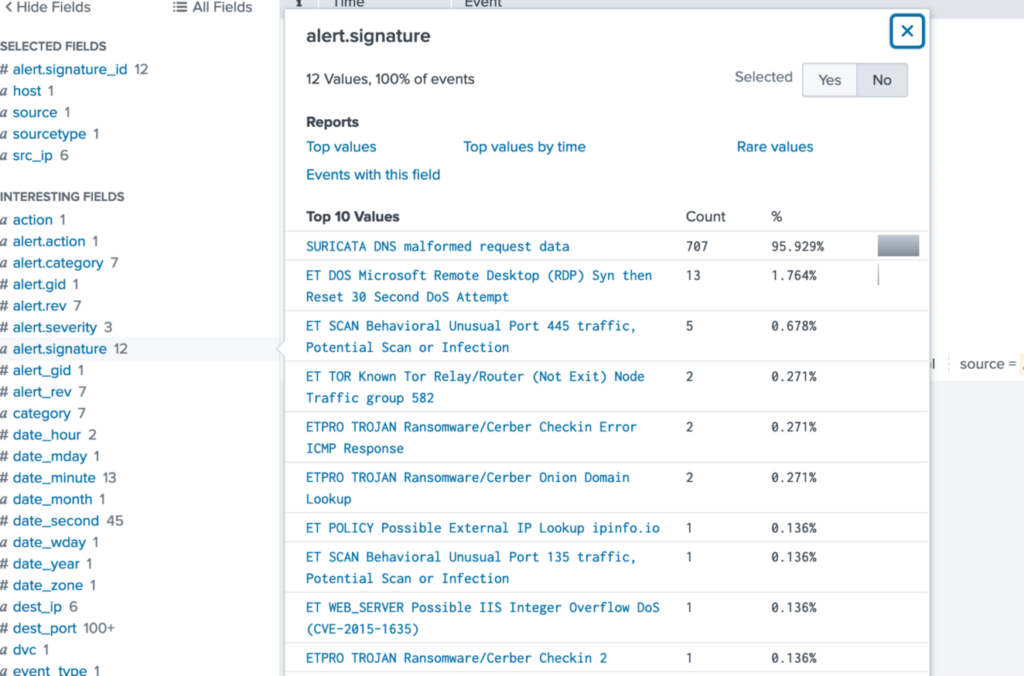
The alert.signature field stands out as useful.
We know the malware is called Cerber, so let's check for instances of that string in the alert signatures.
index="botsv1" source="/var/log/suricata/eve.json" "alert.signature"="*Cerber*"
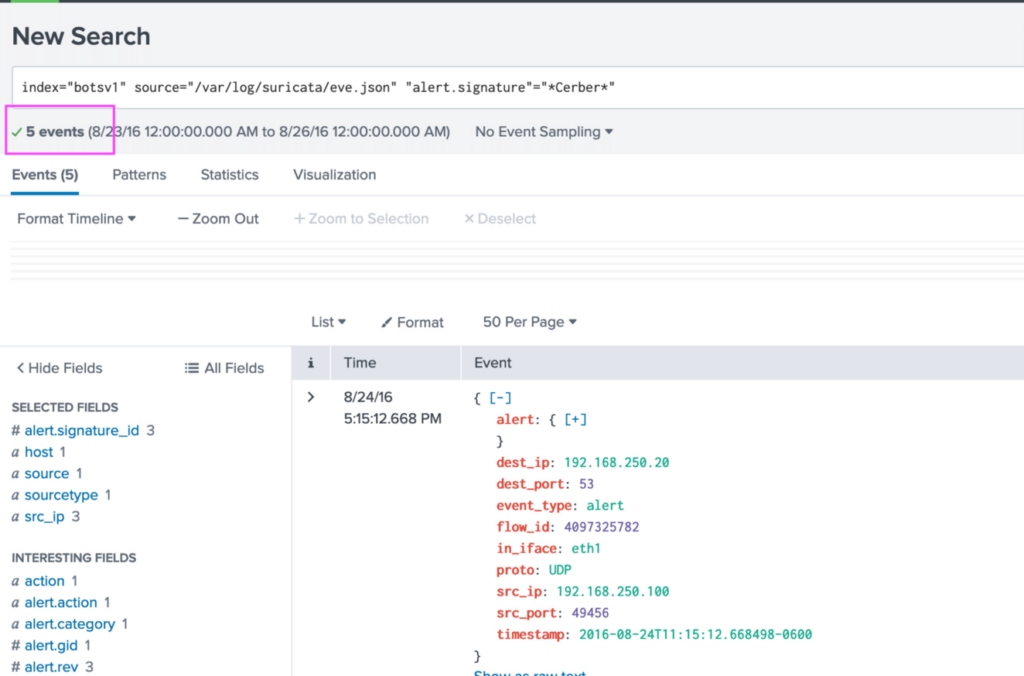
This narrows down the events quite a lot. Thanks to Splunk's dashboard, its easy to see which signature was alerted on the fewest number of times.
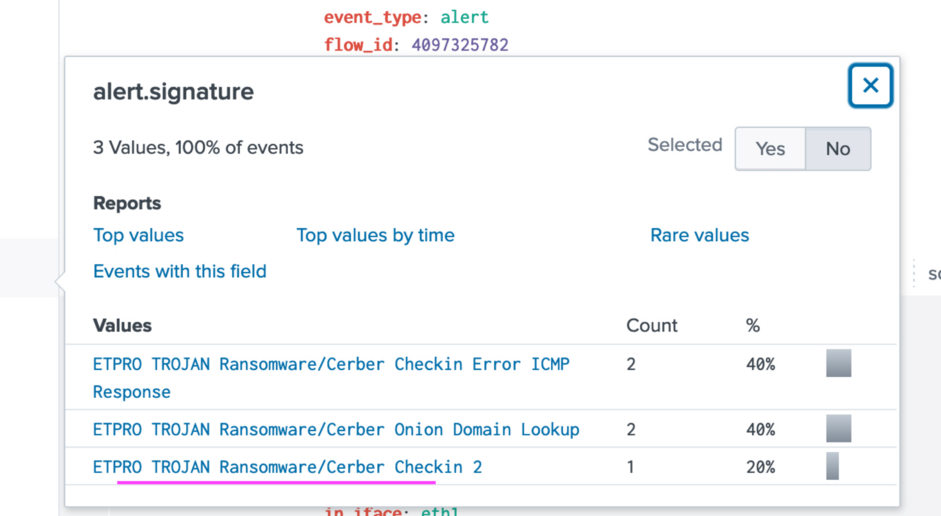
Answer: The ID for that signature (found in the alert.signature_id field) is 2816763 or ETPRO TROJAN Ransomware/Cerber Checkin 2.
Question 3: What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase?
Now that we have the IP Bob's machine was using the day of the attack, we can analyze the DNS queries made from that machine to look for suspicious domain names. An A query is probably the most common type of DNS query and it resolves a domain name to its corresponding IP address.
We'll use the sort, _time, and table commands to sort the queries by their timestamps. We'll also exclude some "noise" related strings like windows, microsoft, and waynecorplocal.
index="botsv1" source="stream:dns" src_ip="192.168.250.100" "query_type{}"=A NOT query IN ("*windows*", "*waynecorpinc*", "*microsoft*")
| sort _time
| table _time, query
Looking through the table with 28 items, one of the domain name immediately stands out as it contains the name of the ransomware:
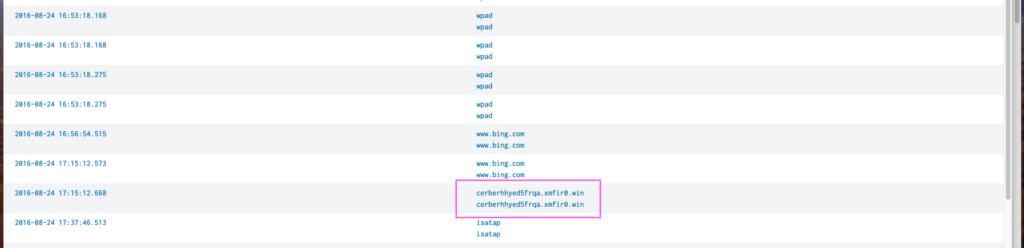
Answer: The FQDN is cerberhhyed5frqa.xmfir0.win.
Question 4: What was the first suspicious domain visited by we8105desk on 24AUG2016?
Using stream:dns sourcetype, we look once again for A queries from Bob's machine on Aug 24th and sort them by time, while removing some of the noise.
index="botsv1" source="stream:dns" src_ip="192.168.250.100" "query_type{}"=A NOT query IN ("*windows*", "*waynecorpinc*", "*microsoft*")
| sort _time
| table _time, query
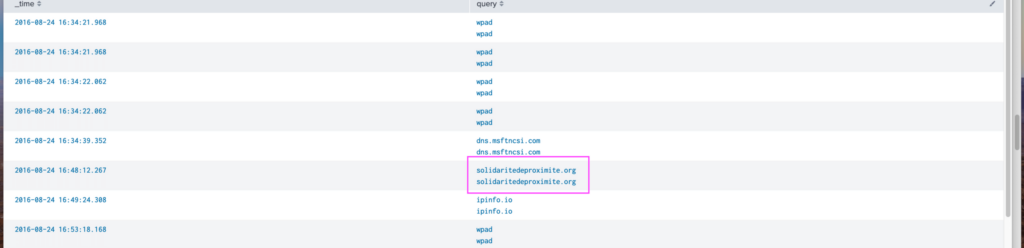
At this point, I didn't know what wpad was. I didn't think it was malicious and a quick Google search confirms that. So, wpad stands for Web Proxy Auto-Discovery and it's a protocol used by clients on a network to automatically discover the URL of a proxy configuration file using DNS or DHCP. IPinfo is an IP address data provider and dns.msftncsi.com is used by Windows devices to check for network connectivity. All of this normal activity singles out solidaritedeproximite.org.
Answer: The first suspicous domain visited that day was solidaritedeproximite.org.
Question 5: During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length of the value of this field?
Because we're looking for an entire script, it will likely be a very long field length. So we can sort events where the CommandLine field has a value, coming from Bob's host machine, and evaluate the lengths of the CommandLine fields and then sort the CommandLine fields by their lengths.
The command with the longest length will be at the top of our table.
index="botsv1" source="WinEventLog:Microsoft-Windows-Sysmon/Operational" host="we8105desk" CommandLine="*"
| eval field_length = length(CommandLine)
| sort field_length
| table _time CommandLine field_length
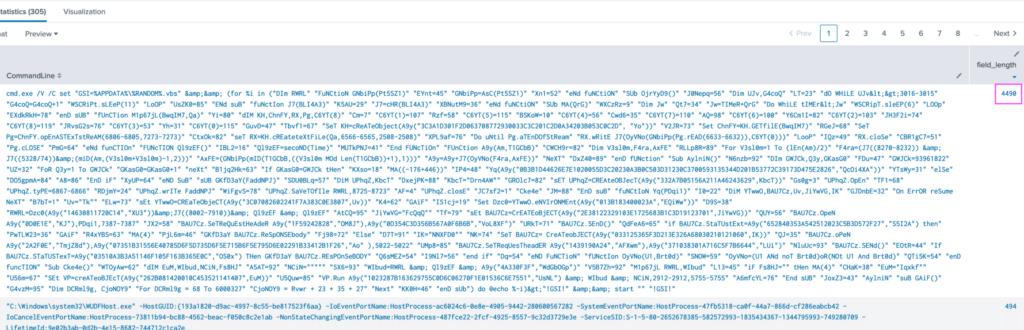
Our table shows the VBS script, and the length of the value for that field is 4490.
Answer: The length of the value for that field is 4490.
Question 6: What is the name of the USB key inserted by Bob Smith?
Had to search Splunks community answers for this one, I found this:
source="winregistry" "HKLM\\SOFTWARE\\Microsoft\\WindowsNT\\CurrentVersion\\EMDMgmt\\" OR "HKLM\\SOFTWARE\\Microsoft\\Windows Portable Devices\\Devices\\" OR "HKLM\\SYSTEM\\ControlSet001\\Control\\DeviceClasses\\" OR "HKLM\\SYSTEM\\ControlSet001\\Enum\\STORAGE\\Volume\\" OR "HKLM\\SYSTEM\\ControlSet001\\Enum\\USB\\VID_111D&PID_0000\\" OR "HKLM\\SYSTEM\\ControlSet001\\Enum\\USBSTOR\\" OR "HKLM\\SYSTEM\\ControlSet001\\Enum\\WpdBusEnumRoot\\UMB\\" OR "HKLM\\SYSTEM\\ControlSet002\\Control\\DeviceClasses\\" OR "HKLM\\SYSTEM\\ControlSet002\\Enum\\STORAGE\\Volume\\" OR "HKLM\\SYSTEM\\ControlSet002\\Enum\\USB\\VID_111D&PID_0000" OR "HKLM\\SYSTEM\\ControlSet002\\Enum\\USBSTOR\\" OR "HKLM\\SYSTEM\\ControlSet002\\Enum\\WpdBusEnumRoot\\UMB\\" OR "HKLM\\SYSTEM\\CurrentControlSet\\Control\\DeviceClasses\\" OR "HKLM\\SYSTEM\\CurrentControlSet\\Enum\\STORAGE\\Volume\\" OR "HKLM\\SYSTEM\\CurrentControlSet\\Enum\\USB\\VID_111D&PID_0000\\" OR "HKLM\\SYSTEM\\CurrentControlSet\\Enum\\USBSTOR\\" OR "HKLM\\SYSTEM\\ CurrentControlSet\\Enum\\WpdBusEnumRoot\\UMB" "friendlyname"
I also found out that the "friendlyname" field in the HKLM\SYSTEM\CurrentControlSet\Enum\USB\ registry can be useful to finding the actual name of the USB. So I searched for that string as well.
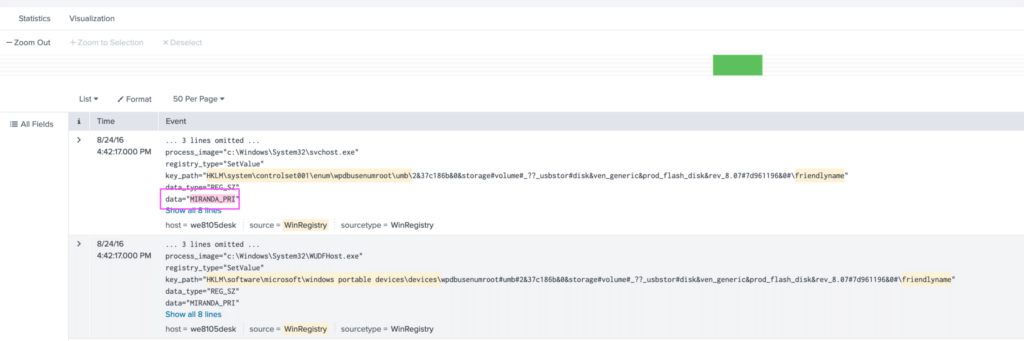
We can see in the data field, MIRANDA_PRI, which is the name of the USB. If we remember from the scenario description, Bob initially opened a file called Miranda_Tate_unveiled.dotm, so the name Miranda stuck out immediately.
Answer: The name of the USB key inserted by Bob was MIRANDA_PRI.
Question 7: Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IPv4 address of the file server?
When looking through the data in previous searches, I noticed that the format for servers at this company is weXXXXsrv. So we'll look for events originating from Bob's machine, where the destination has those specific strings, and sort the events by time.
index="botsv1" host="we8105desk" direction=outbound dest="*we*srv*" | sort _time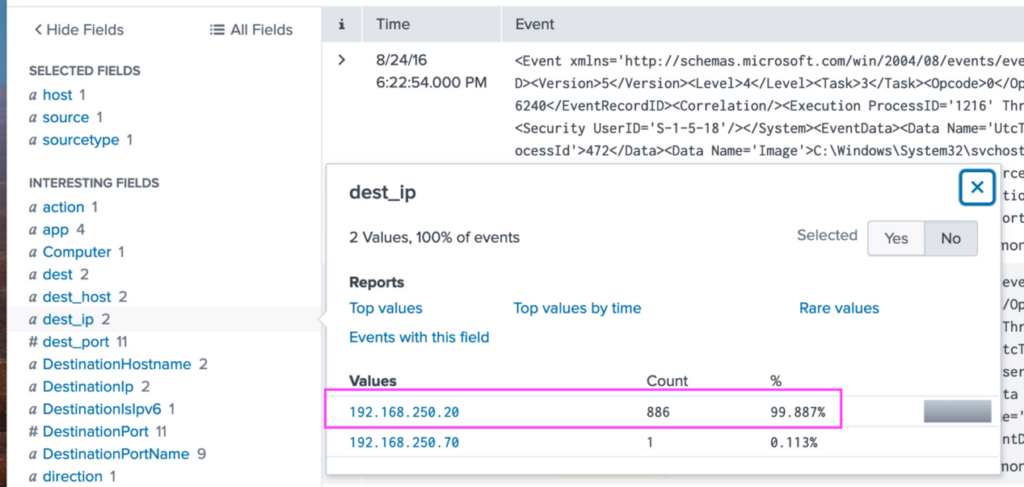
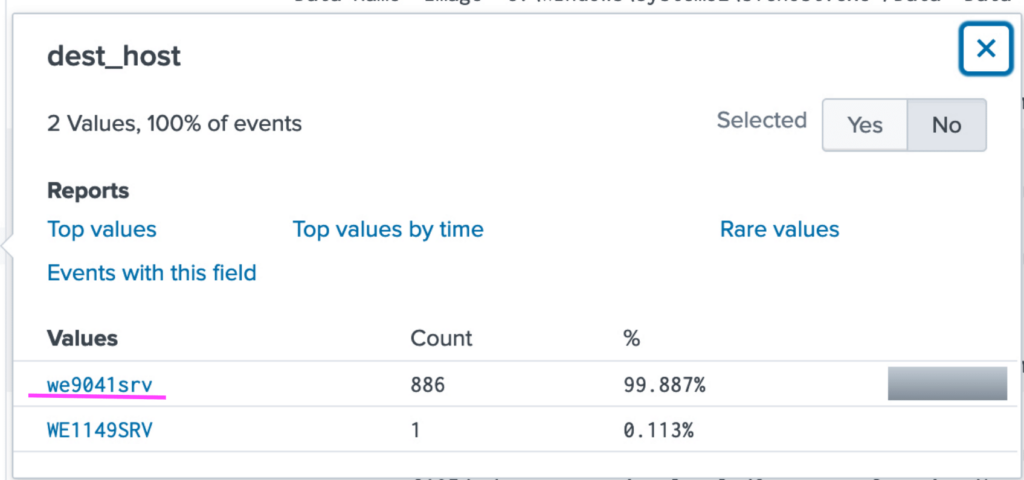
From this search, we find that the IP of the remote server is 192.168.250.20 and it's hostname is we9041srv.
Answer: The IP of the remote server is 192.168.250.20.
Question 8: How many distinct PDFs did the ransomware encrypt on the remote file server?
Because we're dealing with a remote file server (so network shares), we'll use Windows Event ID 5145 (A network share object was checked to see whether client can be granted desired access.) This event offers a more granular view of the actual file that was accessed than 5140 (A network share object was accessed), which will only show you the share name.
We're using the remote server that Bobs machine was connected to during the time period of the attack as the host, which we found in the last question. The source will be WinEventLog:Security as we're looking for audit events related to file access and modification. We are also only looking for PDF's, so I included that string in the search.
index="botsv1" source="wineventlog:security" host="we9041srv" EventCode=5145 "*.pdf"
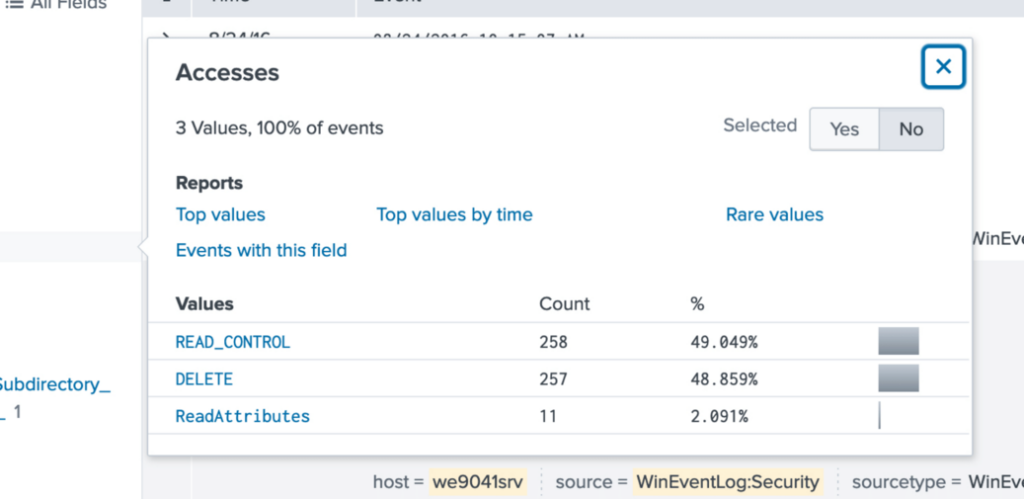
We can see there are only 3 Access types listed from these specific events and files in the Accesses field.
We can view the distinct values of the Relative_Target_Name field (the filename), which should tell us the number of different files.
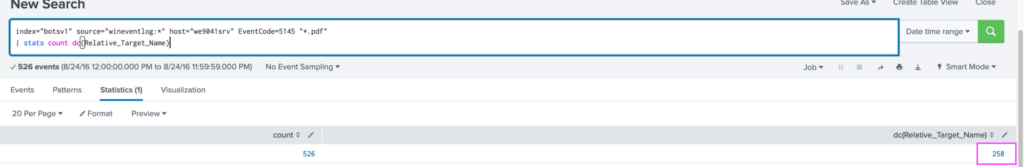
index="botsv1" source="wineventlog:*" host="we9041srv" EventCode=5145 "*.pdf"
| stats count dc(Relative_Target_Name) This query shows us there are 258 distinct files.
For encrypting files, I expected to see something like WRITE_DATA Access, meaning that the permissions exist for those files to be modified. In looking through the available fields, I see WriteAttributes and WriteData__or_AddFile_1 and notice that they only list 257 files. So while there are 258 different PDF files, only 257 of them would be able to be encrypted.
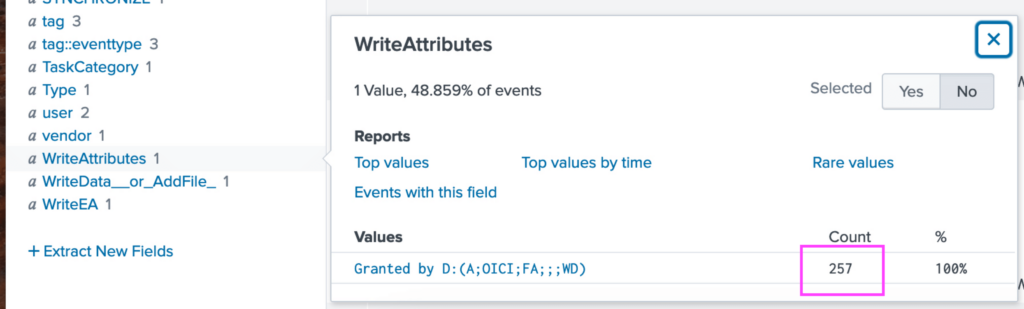
Answer: 257 distinct PDFs were encrypted on the remote file server.
Question 9: The VBscript found in question 204 launches 121214.tmp. What is the ParentProcessId of this initial launch?
We'll use Sysmon data to look for events that have a ParentProcessID value and where the string 121214.tmp is present in the CommandLine field. We'll sort by time just to make finding the script launch slightly easier.
index="botsv1" source="wineventlog:microsoft-windows-sysmon/operational" ParentProcessId="*" CommandLine="*121214.tmp*"
| sort _time

This query narrowed the events down quite a bit and we can easily see that wscript.exe is responsible for running the VBS script. It has a ParentProcessId of 3968.
Answer: The ParentProcessId of this initial launch was 3968.
Question 10: The Cerber ransomware encrypts files located in Bob Smith's Windows profile. How many .txt files does it encrypt?
We'll use Sysmon event logs again to look for instances of .txt files being accessed from Bob Smith's profile. Because they're on his profile, we can specify the file_path field and count the number of file names:
index="botsv1" source="wineventlog:microsoft-windows-sysmon/operational" ".txt" file_path="*bob.smith.WAYNECORPINC*"
| stats count(file_name)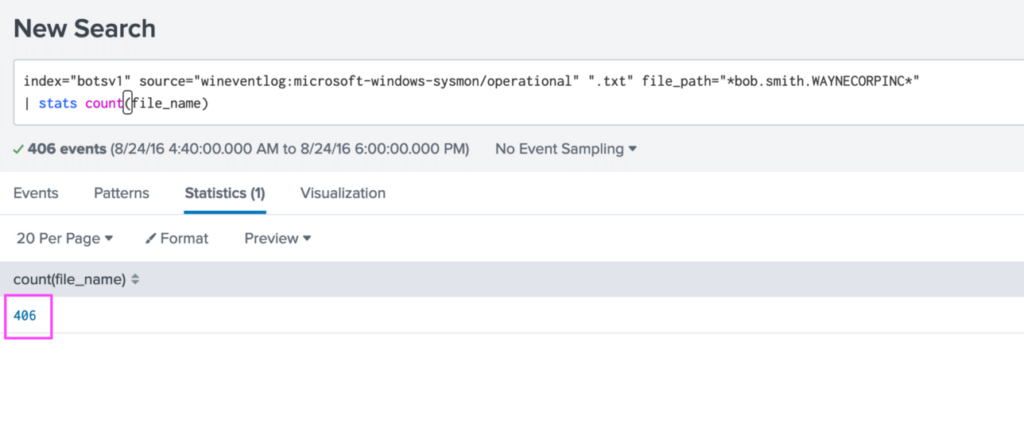
Answer: 406 .txt files were encrypted.
Question 11: The malware downloads a file that contains the Cerber ransomware cryptor code. What is the name of that file?
This file was downloaded from the internet, so we'll use Suricata (Suricata generates logs from network traffic) logs from Bob's infected machine's IP, event_type as http, and events using HTTP GET method since we're downloading a file.
index="botsv1" source="/var/log/suricata/eve.json" src_ip="192.168.250.100" event_type=http "http.http_method"=GET Let's use a table and some useful fields we found to view the results better:
index="botsv1" source="/var/log/suricata/eve.json" src_ip="192.168.250.100" event_type=http "http.http_method"=GET
| table http.url, http.hostname, dest

Now we can see the suspicious domain we found earlier, solidaritedeproximite.org, as well as an IP we hadn't noticed, 92.222.104.182. Both are associated with the file mhtr.jpg, our encryptor code file. It's pretty common for attackers to use non-executable files to raise less suspicions.
Answer: The name of the file is mhtr.jpg.
Question 12: Now that you know the name of the ransomware's encryptor file, what obfuscation technique does it likely use?
Because the encryptor file was a .jpg file or an image file, the likely obfuscation technique being used is called Steganography. This is where the code is concealed within the data of the image.
Answer: The obfuscation technique likely used is steganography.
Cover image by DC Studio on Freepick
